An Alternative to Client-Side Encryption
Client-side encryption has long been the gold standard for data protection. It keeps third-party infrastructure or storage providers from viewing your sensitive data, and it helps prevent the exposure of personal information in cyberattacks.
But client-side encryption also has its drawbacks:
- It requires regular key rotation and well-defined key management policies, which bring cost and complexity.
- Encrypted data is stored as a whole file in a single location, meaning that it can be deleted, tampered with, exfiltrated for a well-resourced adversary to decrypt over time or with a stolen key.
- Encrypted data can easily be re-encrypted in a ransomware attack, cutting off your access to your own data.
- Client-side encryption wasn’t designed to maintain data availability, so it doesn’t help prevent downtime in the face of outages, human errors, and other disruptions.
There are also major downsides to using client-side encryption in app development. We’ll explore them below, and we’ll explain a new alternative to client-side encryption.
Client-side encryption: when the gold standard slows down your developers
Being fast to market is one of the key performance indexes of modern application development. The higher your team’s velocity, the more economically your ideas will be brought to life.
Although it offers strong data privacy benefits, client-side encryption slows down app development. Encryption and decryption need to be introduced to every process that reads or writes data, and key rotation needs to be implemented to align with encryption policies.
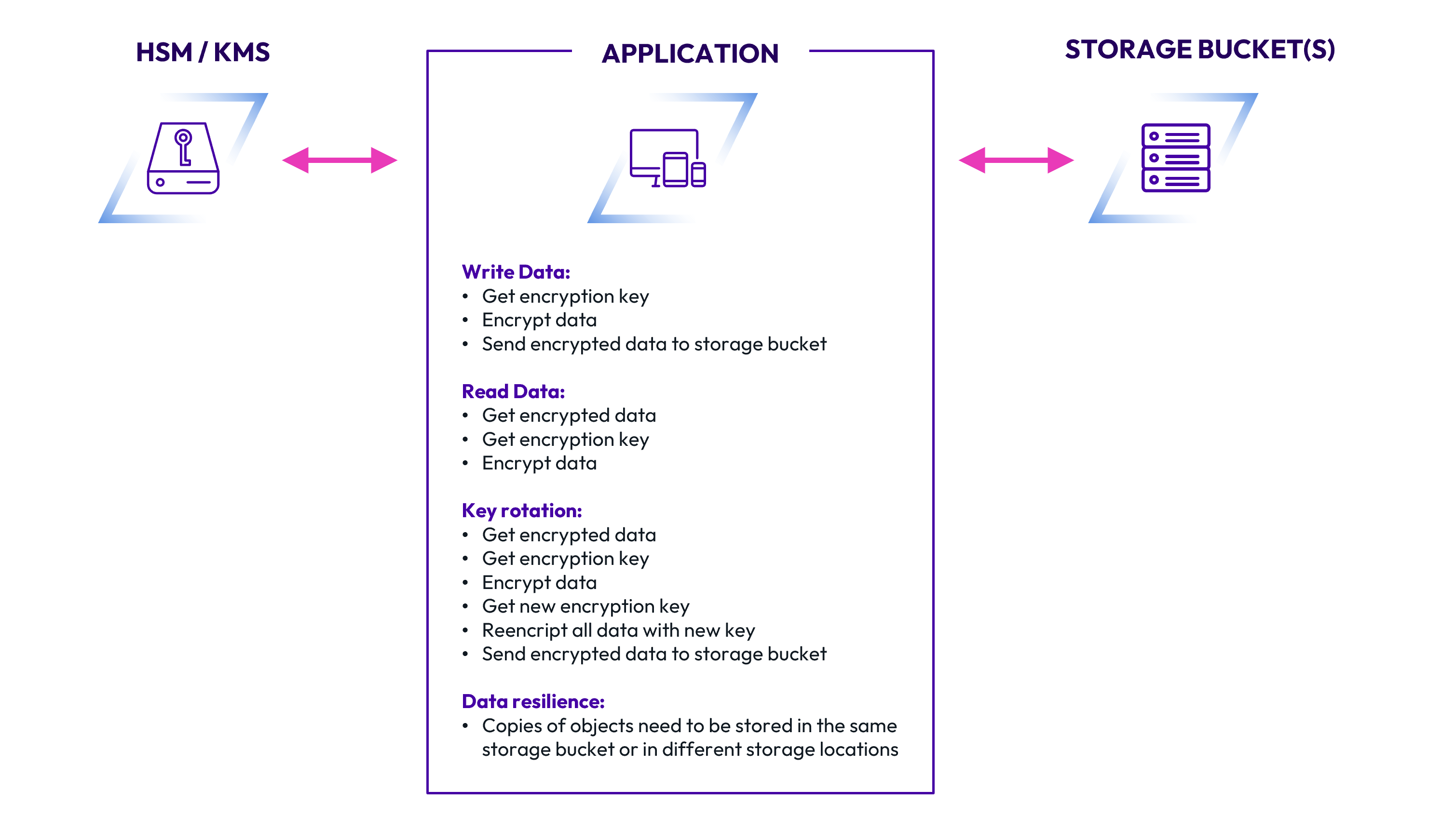
Integrating client-side encryption into your application can be a long part of the development cycle and ultimately add months to your timeline. The continuous key management processes and the re-encryption of data make production environments more challenging, and the burden on the application is high:
- Writing data. This includes getting an encryption key, encrypting data, and then sending that encrypted data to a storage location.
- Reading data. This includes retrieving the encrypted data, retrieving the encryption key, and decrypting the data.
- Performing key rotation. Key rotation is a particularly onerous task, requiring the app to retrieve encrypted data, retrieve the encryption key, decrypt the data, get a new encryption key, reencrypt all data with that new key, and finally send the encrypted data back to the storage location.
- Fast processing and performance. Constant encryption and decryption in an application can create a heavy processing load, leading to lags in performance.
- Providing data resilience. Copies of objects must be stored in different storage locations for redundancy. Data must also be protected from incidents ranging from ransomware to cloud provider outages and misconfigurations.
In short, implementing client-side encryption in your application is time-consuming and resource-intensive. It also doesn’t offer data resilience or availability. Client-side encryption simply wasn’t designed to protect against issues like provider outages, ransomware attacks, and data tampering in your storage locations.
ShardSecure: an innovative alternative to client-side encryption
ShardSecure fulfills the same purpose as client-side encryption, offering strong data confidentiality and integrity. But it also provides data availability and strong resilience in the face of threats like cyberattacks, and the demands on developers are far fewer.
Instead of having the application continuously perform encryption, decryption, key rotation, and more, developers simply need to have it read from and write to the storage location.
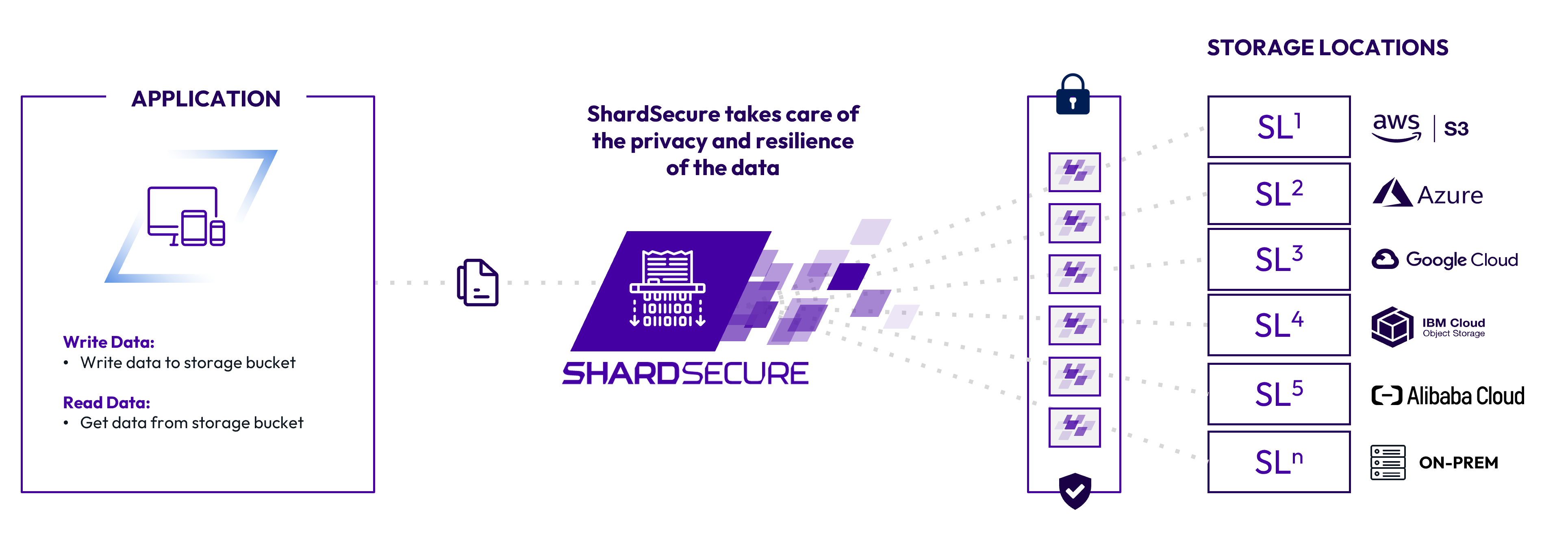
Advanced data protection and resilience
To support data privacy, our three-step microsharding process shreds files into four-byte microshards and then distributes those microshards across organizations’ own storage locations in hybrid- and multi-cloud environments. There is no need for key rotation or re-encryption at any point.
Microsharding also offers strong data resilience, helping to maintain data availability during events like provider outages and ransomware attacks. With multiple data integrity checks and transparent reassembly of compromised storage locations, we ensure that your users can continue working without interruption.
Ease of implementation
ShardSecure is easy to integrate, either on its own or with your existing client-side encryption for increased defense-in-depth. (We can work as either a replacement for and a supplement to client-side encryption, depending on your needs.)
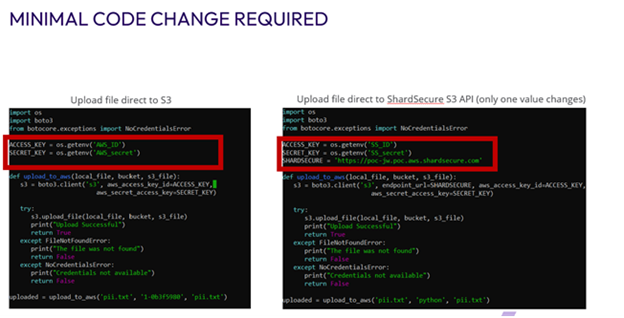
Our solution exposes an S3-compatible API for your applications, allowing for easy migration across different cloud service providers. Your engineers do not need to take additional steps to implement client-side encryption. You can deploy ShardSecure easily with all kinds of applications.
To reconfigure an application for ShardSecure’s API, you will only need to make one change: Instead of pointing read/write operations to your storage location, you’ll change a single line of code and point them to ShardSecure instead. The rest of the code remains the same. There is no need to make any other changes beyond that one line.
Conclusion
Client-side encryption can slow down even the most agile development teams. With ShardSecure, you can augment or replace your client-side encryption without compromising on data security or changing your application design. Your data stays protected and remains under your control.
For more information about how ShardSecure supports data privacy and data resilience, check out these resources:
- Our white paper on complementing or replacing encryption with microsharding
- Our solution brief on strengthening data resilience
- Our FAQ on encryption and microsharding
- And much more.







