ShardSecure Platform
Simplify unstructured data security, enhance privacy and ensure resilience for hybrid- and multi-cloud environments.
Agentless File Level Encryption
- Protection for files, folders, and storage locations on-prem and in the cloud
- Advanced protection for unstructured data without the need for agents
- Data security for application teams
- Secure AI/ML model and training data
- FIPS 140-3 L1 certification
Ransomware Protection
- Keep data safe and accessible during ransomware attacks, outages, unauthorized deletion, and other availability issues
- Protect against data tampering with data integrity checks and self-healing data
- Store data in hybrid and multi-cloud architectures
- No more operational downtime
Advanced Data Privacy
- Separate data owner from infrastructure owner
- Support for regulatory compliance, including the GDPR/Schrems II and US state privacy laws
- Maintain data confidentiality in cross-border data transfers
- Address data sovereignty and residency concerns in on-prem, hybrid-cloud, and multi-cloud storage
NEW! ShardSecure Spark
Elevate Your Data Security, Privacy, and Resilience with ShardSecure Spark! It's free for organizations with a data protection requirement of up to 10 GB!
Enjoy strong security on-premises, in the cloud, and in hybrid- or multi-cloud architectures.
Protect your data anywhere while lowering costs and reducing complexity.
Agentless file-level protection, robust data resilience, native ransomware protection, support with cross-border compliance and more.
Strengthen your security and control of your data today.

Let's talk
Schedule a demoHow it works
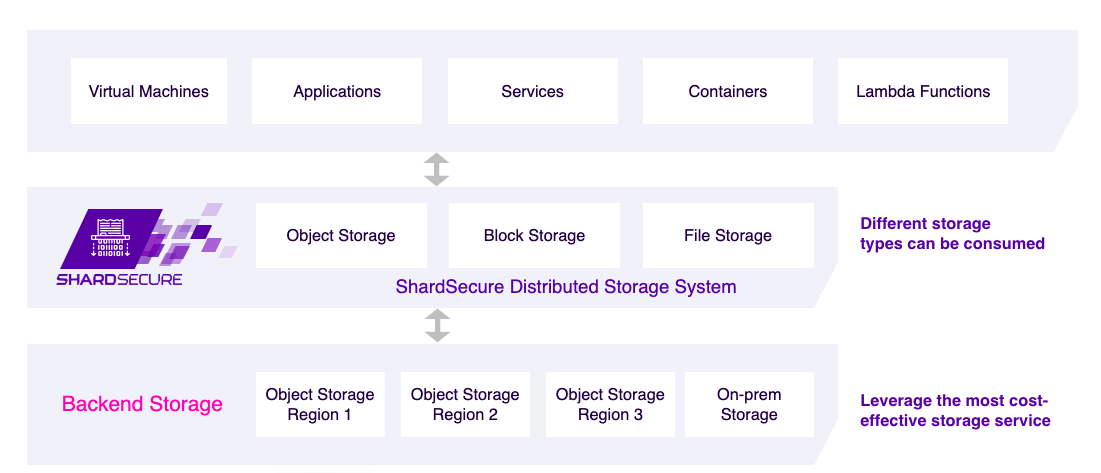
Your data is everywhere: applications, databases, servers. Our solution simply presents itself to them as a cloud and/or network storage location accessible through our S3-compatible API and iSCSI module.
Shred
Your data is first compressed, then shredded into microshards, which can be as small as four bytes and are too small to contain sensitive data.
Mix
The microshards are then mixed into multiple logical containers with poison data added to make unauthorized re-assembly exponentially more difficult.
Distribute
Your microsharded data is distributed to multiple storage locations of your choosing in multi-cloud, multi-region, or hybrid cloud environments.