When asked why he robbed banks, accomplished criminal Willie Sutton simply said, "Because that’s where the money is."
We’re now beginning to hear of cloud ransomware attacks because, increasingly, “that’s where the data is.” Cybersecurity Ventures predicts that 50% of the world’s data will be stored in the cloud by 2025, up from approximately 25% in 2015. Clearly the migration of data to the cloud began years ago, but COVID accelerated that trend and now there is an unmistakable, huge shift of data from on-premises to the cloud.
Security professionals need to prepare for the fact that as more data moves to the cloud, threat actors are going to shift increasingly from ransomware on the endpoint to ransomware in the cloud. Today, cloud ransomware has remained under the radar with no publicly disclosed incidents. However, multiple ShardSecure partners, including a cloud service provider (CSP) and a large incident response company, have told us they have seen real-world incidents of cloud ransomware.
A changing threat landscape
Cloud ransomware can work the same way as on-premises ransomware. For example, threat actors can infect a virtual machine (VM) as they would an on-premises server and ransom all the storage. However, there are some techniques that apply only to the cloud. Here’s a scenario that targets cloud-based encryption and uses one of the features of the cloud, the CSP’s key management services (KMS).
On-premises, you control your own keys and your own encryption. In the cloud, customers often let the CSP manage their keys to encrypt the data. Using compromised credentials, an attacker can have the CSP encrypt the data with a key controlled by the attacker. The attacker then changes permissions on the key so that it is unusable, and the data cannot be decrypted until payment is made.
This is just one example, but there are other techniques threat actors may develop to launch ransomware attacks in cloud environments. So, some of your techniques to defend against these attacks should be different as well.
The other aspect that is different in the cloud is the division of responsibility between the CSP and the user. You may think that your CSP is keeping you safe and you don’t have to worry. But CSPs operate with a shared responsibility model which varies based on different cloud environments. This complexity can make it difficult to keep up with what you are responsible for, which leads to gaps and vulnerabilities. However, as the chart below shows, data is the customer’s responsibility regardless of the cloud service used.
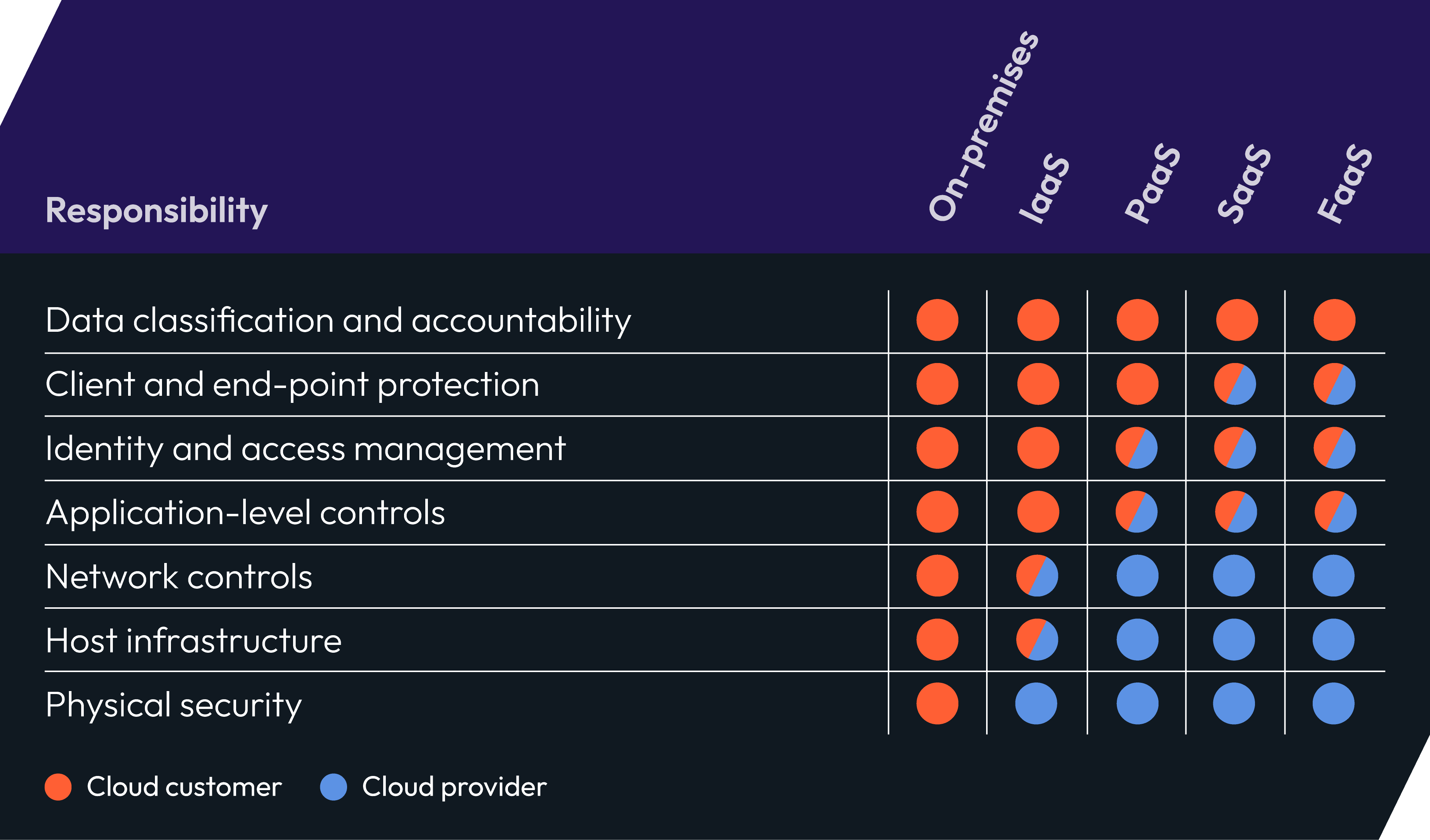 Diagram adapted from 'Center for Internet Security | Shared responsibility for cloud security: What you need to know'.
Diagram adapted from 'Center for Internet Security | Shared responsibility for cloud security: What you need to know'.
A good rule of thumb is that the CSP is responsible for security of the cloud, and you are responsible for security in the cloud—and in the cloud means data and server-side encryption. So, what can you do to better protect your data from cloud ransomware?
How ShardSecure protects against cloud ransomware
Today, many ransomware attacks take a two-pronged approach, encrypting it and exfiltrating it for double extortion. The idea is that if the victim doesn’t pay the ransom, the attacker will publicly release the data.
The ShardSecure platform helps mitigate both aspects of these cloud ransomware attacks. First, our self-healing feature automatically reconstructs data that has been tampered with or lost in an attack, preventing downtime. Second, our advanced data privacy makes sensitive data unintelligible and unexploitable to any unauthorized users, including ransomware attackers.
Wherever you are in your cloud journey, you can get started now to mitigate the risk of cloud ransomware. To learn more, check out our ransomware solution page.

.jpg)






