Who is responsible for data security in the cloud?
Cybersecurity Ventures predicts that 50% of the world’s data will be stored in the cloud by 2025, up from approximately 25% in 2015. Protecting that data presents many challenges, especially as cyber threats escalate and the average cost of a data breach reaches a record high of $4.35 million.
Today, it’s more important than ever for organizations to understand where their data resides, who is responsible for that data, and how they can better protect it in the cloud.
Data security in the cloud is a huge issue
Cloud Security Alliance (CSA) researchers report that 89% of organizations host sensitive data or workloads in the cloud. Yet, alarmingly, only 39% of organizations have high levels of confidence in their cloud data security, and only 4% report sufficient security for 100% of their data in the cloud. Additionally, 92% of security professionals whose organizations have experienced a data breach believe that they will experience another in the coming 12 months.
These concerns are well-founded. If you look at some of the largest cloud security breaches in 2021, massive amounts of data and sensitive user information have been exposed. Even the most advanced enterprises are not safe from persistent cyber attackers who take advantage of misconfigurations, security flaws, and user errors to encrypt, destroy, or leak valuable information. Without robust cloud security, your sensitive data is simply not secure.
The shared responsibility model can cause confusion
Cloud data protection can be especially challenging because the lines of responsibility for protecting that data are often blurred. Some organizations may assume that their cloud service provider (CSP) will protect them — but CSPs operate with a shared responsibility model. Many organizations do not understand exactly which security measures they’re responsible for and which ones the CSP manages under this model. Additionally, as CSPs evolve and add more services as well as tools to configure, manage, and secure those services, who is responsible for what will likely become even more confusing.
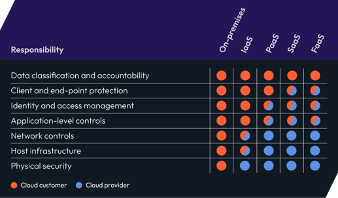
To avoid gaps in protection, a good rule of thumb is that the CSP is responsible for security of the cloud (the platform, service, and offerings), while organizations are responsible for security in the cloud (especially their own data). Having your own tools to protect your data in the cloud will ensure your data is consistently secure from threats.
Multi-cloud environments add complexity
It’s not just companies moving data to a single cloud location, either. Nearly 90% of organizations report having a multi-cloud strategy, and 67% of IT professionals say their organizations will maintain a hybrid-cloud strategy moving forward. Protecting data wherever it resides is paramount, but these multi- and hybrid-cloud strategies add complexity. The more clouds an organization uses, the harder it is to keep track of their data assets in those clouds — and the less their traditional data security techniques hold up.
Another challenge in multi-cloud environments is that shared responsibility models can vary from one CSP to another. Different policies among different providers introduce additional complexity for security and risk management teams.
According to Gartner, “Through 2025, at least 95% of cloud security failures will be the customer’s fault.” This prediction should serve as a wakeup call to organizations that they need to get a better handle on their cloud data security. That includes knowing where their data is, understanding their responsibility, and implementing and enforcing policies and practices to secure their data in the cloud and reduce risk.
Protecting your data in the cloud with ShardSecure
At ShardSecure, we protect your data more effectively against attacks, including double-extortion ransomware attacks, within multi-cloud and hybrid-cloud environments.
Our Microshard™ technology works transparently and in real-time to microshard your data, making it unintelligible to unauthorized users and secure from compromise. We can also be integrated with your own encryption solutions for a defense-in-depth approach.
Additionally, we maintain strong cloud data integrity. Our self-healing data automatically reconstructs affected data whenever it’s tampered with, deleted, or encrypted with ransomware, with no need to manually restore data from backups. To your users, nothing has changed. They can open and work with their microsharded files just as they had before the attacks. They won’t even notice anything is amiss.
Ultimately, the responsibility for your data in the cloud lies with you. Let us help shoulder that burden with a microsharding solution that offers the data security and resilience your cloud data needs.
Sources
The World Will Store 200 Zettabytes of Data by 2025 | Cybercrime MagazineCost of a Data Breach 2022 Report | IBM
The State of Cloud Data Security | CSA
Understanding Cloud Data Security and Priorities | CSA
Top 5 Cloud Security Breaches (and Lessons) | Cybertalk.org
Shared Responsibility for Cloud Security: What You Need to Know | CIS
Cloud Computing Trends: Flexera 2022 State of the Cloud Report | Flexera
Hornetsecurity Hybrid Cloud Adoption Survey | Hornetsecurity
2022 Thales Cloud Security Study | Thales, 451 Group, S&P Global
Is the Cloud Secure? | Gartner







