Cloud-based ransomware? We have an answer
TL;DR
When you microshard your sensitive data in the cloud, we can help you remain operational and maintain your data integrity during a cloud-based ransomware attack.
Whatever you do, don’t click that link
Imagine this scenario: An administrator at your cloud provider is tricked into executing a script that encrypts all of your microsharded data. Now what? We automatically revert the affected microsharded files back to their last known good state, that’s what.
To your users nothing has changed. They can open and work with their microsharded files just as they had before the attack. They shouldn’t even notice anything is amiss.
From a security perspective, there is 0 reason for Microshard data to change at rest, so any modification is an indicator of compromise. We can notify your SOC and feed alerts to your SIEM or SOAR to initiate your response workflow. You also have the ability of using us to move your Microshard data from the affected storage location to an unaffected location while you remediate the incident.
How do we do this?
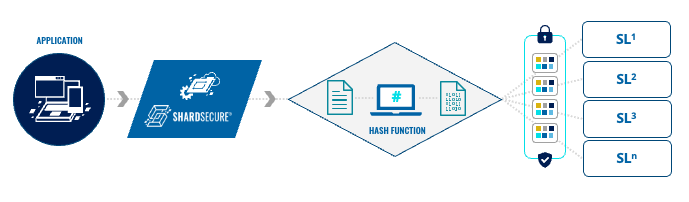
I’m glad you asked. But first, let’s level set on how our MicroshardTM technology works. We shred files into four-byte microshards, mix them into multiple Microshard containers, and then, distribute the containers to multiple storage locations. (Take a look at this solution brief for more information.)
We generate a hash of every container for a given file before we distribute the containers to storage. We hash those containers again and compare the values just before we reassemble the containers to present the file to the user.
If there’s a mismatch, we will simply revert any microsharded data back to its last known good state based upon the original hash. Then reassemble the file for the user. It doesn’t matter to us if the Microshard container has been encrypted, modified, or even deleted.
A note about context
The topic and implications of ransomware are very serious, so I want to be clear about the context in which we can help you. Our capability is primarily focused on reverting unauthorized modifications to or deletions of the backend Microshard data. A scenario such as the one above, a breach of a storage location, or accidental or intentional exposure of a storage location online are all areas where we can help you remain operational and maintain data integrity.
No one technology will neutralize the ransomware threat. A strong defense-in-depth architecture is still your best defense. And we believe that we are in a unique position to help you mitigate your cloud ransomware risk.
To learn more, be sure to check out this demo video, our solution brief about cloud-based ransomware, and click the link above to book a live demo.






